Every day, families share photos, sign into apps, and store personal details online without thinking twice. We lock our homes and protect our valuables, yet our digital lives stay wide open in ways we hardly notice. Most people assume real danger only comes from hackers or major cyberattacks. But in reality, many risks start with simple mistakes, such as an exposed file, a careless post, or an unsafe app installed by a child. Despite living in a connected world, many parents still don’t understand the threat or even know what is a data leak.
What is a data leak?
When some private information is shown to unauthorized persons, it can be called a data leak. This exposure normally occurs because of poor security controls. Data leaks are often accidental and happen when systems, apps, or users aren’t properly secured. Even small mistakes, like a wrong setting or browsing unsafe sites, can expose private information.
Data leakage does not imply the same thing as a data breach. A breach entails a criminal intrusion. Hackers gain entry into a secure system and loot data. Information is leaked when information is available without being hacked intentionally. Like, there may be improper access controls on a server. An accidental sharing of a document may occur. A child may overshare online. All of them disclose data, yet their source are different.
A variety of information may be divulged in a data leak. Mostly, personal information consists of names, ages, addresses, and school. Bank numbers, cards, and transaction records constitute financial information. Similarly, Location data involves home location, live location, or route directions. Sometimes, Usernames and passwords, along with authentication tokens, can be found in the account data. Data from the devices contains IP addresses, browsing history, and files saved. All in all, Leaked information can lead to fraud, impersonation, or targeted scams. The harm may have a long-lasting effect on children and adults.
Data leaks happen worldwide. Government systems, hospitals, schools, and social networks have all experienced leaks. Such accidents demonstrate that there are no users or families that will remain completely safe. The first level of defence is awareness.
Common causes of data leaks
The majority of data breaches are a result of mere issues. In addition, many leaks occur because of human error or unsafe internet practices. It is more dangerous to families since children and teenagers are able to roam the internet without restraint. These are the reasons that can be found in real cases.
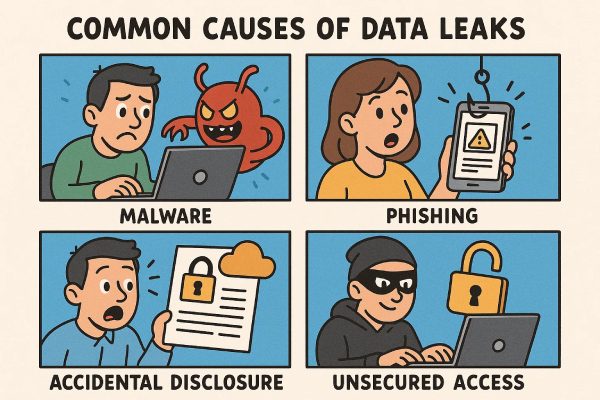


Weak passwords or reused login credentials:
Poor passwords continue to be the leading reason for exposure. Simple passwords are convenient to many users. Moreover, Children have a tendency to repeat passwords on various platforms. However, this has a spill-over effect when a single website breaches the user database of its site. Bad guys will use the same credentials in a large number of services with the hope of a match. Attackers use a method called credential stuffing when leaked passwords are reused. It is effective as a number of individuals use the same passwords. A single leak from a gaming account can expose school, email, and social media accounts. Thus, families have to know that password habits have a direct impact on security.
Unsafe apps or websites:
Most children are downloading free applications without even considering their safety. Others demand unwarranted permissions, including access to contacts, microphones, or locations. Some users have their data shared with third parties for advertising or analysis. In severe repercussions, applications will install background trackers or viruses. Data are also collected silently on unsafe sites. They can document the activity of browsing or use malicious scripts. The imitated download pages are usually spoofed as well-known brands and deceive children into downloading dangerous programs. These activities reveal personal information, and the user is not very aware of this.
Social media oversharing:
One of the most widespread reasons for leaking data within the digital space is oversharing. Children love to update their social sites on a daily basis. They can disclose school uniforms, residential addresses or the schedule of activities. There can be house numbers, family members, or even sensitive documents in the background of the photos. Location tags reveal real-time movement. A good number of children fail to change privacy settings. Strangers can access and store their content in public accounts. Attackers can copy, share, or misuse this information. Excessive disclosure yields permanent online traces. It also makes it more vulnerable to impersonation, harassment, or targeted scams.
Insecure public Wi-Fi and device theft:
Public Wi-Fi networks are portable and not secure. Many lack encryption. Attackers can intercept private information sent over unsecured networks. This entails passwords, messages, and browsing activity. In malls, schools, cafes, and transportation centers, children tend to use public Wi-Fi. They can access sensitive accounts without comprehending the risk. Data in devices is also exposed to device theft. A lost phone may contain saved photos, emails, or passwords. In case the device does not have a very powerful lock, the thief can access all the elements with ease. These threats increase as children expand their use of mobile devices.
Lack of parental supervision or awareness:
There are numerous parents who do not take risks seriously online. Young people tend to play with applications, games, and social sites without supervision. They can become members of unsafe communities or chat rooms. They can access dangerous URLs or save doubtful files. Some children share personal information when talking with strangers online. In the absence of counsel, they fail to notice red flags. Lack of parental awareness increases the chances of accidental leakage. Parents should know that the choice that kids make on the internet has long-term consequences for their safety. Luckily, Parents can prevent many harmful mistakes through regular discussions and monitoring.
Ensure your child’s information stays private and secure.
What happens when a data leak occurs?
When a leak of data occurs, it spreads very fast. Several times, leaked data has been found in open forums, search engines, or file-sharing sites. Hackers are able to replicate the data in a matter of minutes. Part of the leaks find their way to the dark-web markets, where the criminals trade to sell and purchase the stolen information. When shared, the information will be there forever, or cannot be retrieved easily. Families must understand that leaked data may remain online for years and cannot be erased easily.
A report by research gate states, “Data leakage poses serious threats to organi-zations, including significant reputational damage and financial losses.” Similarly, the after effects may be drastic. Crimes like identity theft are common, where the offenders employ the personal information of the victims to deceive them.
From there, they can open accounts, make purchases, or commit fraud. Scams increase after a leak. The victims get phishing-related messages, counterfeit alerts, or fraud calls. Leaked emails and phone numbers often end up in marketing lists, causing spam. Leaked photos or private messages can damage a person’s reputation. This is a high risk to the children, as their social life is delicate.
Cybersecurity reports record many massive leak cases. Such briefings reflect breaches of millions of users of banks, retailers, and social networks. These happenings indicate how prevalent digital exposure is and the need to prevent data leaks.
How to protect yourself from data leaks?
To avoid a data leak, one needs to follow a routine. Some of the most important practices to reduce exposure in families are mentioned here. These enhance online security and reduce the effects of errors.
Strong and unique passwords and 2FA.
The accounts must have a good and distinct password. Keep off of personal information like name or birthday. A password manager assists in managing passwords and also creating secure passwords. There is two-factor authentication (2FA) that provides an additional level of verification. Two-factor authentication can protect you even if a password leaks. These measures guard against typical attacks of accounts.
Do not post personal information on the Internet.
Keep the postings on the internet to a minimum. Do not give out addresses, school information, or routine. Switch off location services unless necessary. Advise the children to make their profiles private. Train them to check the posts prior to posting. Strict precautions will guard against great exposure.
Update devices and applications.
Software updates fix security flaws. The older equipment is at increased risk of data leaks. So, allow automatic upgrading of all family devices. Uninstall unnecessary applications in order to cut down on unnecessary permissions. Check application authorization on a regular basis. These steps reduce vulnerabilities that attackers exploit.
Watch out for suspicious downloads or links.
Phishing emails are likely to appear to be credible. They seek to fool users into typing passwords or downloading malicious installables. Educate family members on how to confirm links, emails, and senders. Similarly, avoid downloading files from unrecognized sources. Promote the use of questions when installing new applications for children. Careful behavior prevents most attacks.
These practices create a good fortification. They minimize daily family exposure to digital activities and enhance family security.
How can parents prevent data leaks for kids?
Children face unique risks online. They communicate very often with their friends, games, and social media. They can post personal information without consideration. Even most adults lack digital awareness. They can share photos of school, schedules of the day, or personal details. They can disclose residential addresses by posting pictures in front of the houses. Such activities may reveal personal information to unknown people.
Parents play the primary role in preventing these risks. Education will enable children to realize risky behavior. Well-defined rules set secure boundaries. Supervision would make sure that children use platforms responsibly. Parental-control tools provide additional protection. Apps like FlashGet Kids have features that can facilitate these objectives.



- App monitoring in FlashGet Kids will allow parents to monitor the apps and websites that children access. This demonstrates unsafe platforms or overuse. It allows parents to identify suspicious applications that ask them to grant them unwarranted permissions. Monitoring also helps to detect damaging content in time.
- Screen-time limits in parental control tools reduce online exposure. The fewer hours spent online, the less the possibility of oversharing or surfing dangerous websites. Boundaries are also useful in ensuring children concentrate on safe and healthy activities. Such controls will safeguard the children against extended use of unsafe spaces.
- Real-time location tracking helps prevent location leaks. Without the use of social media check-ins, parents cannot know the whereabouts of their children. This will save the children the trouble of announcing their location publicly. It also helps in safety in case of an adventure or in case of an emergency.
- Blocking features and web filters prevent entry to malicious sites. The filters prevent spam pages, phishing websites, and unverified downloads. This helps to avoid exposing children to harmful online space. Blocking helps to lessen the exposure to malicious pop-ups or fake advertisements as well.
Parents should use parental-control tools alongside digital education. Also, guardians should educate their children on the importance of privacy. Families can use digital tools to reinforce safe online behavior. This mixture provides a balanced and feasible solution. It assists families in avoiding information leakages and long-term security.
Conclusion
Data leaks threaten personal security. And they also reveal confidential data to third-party. As children are spending more hours online, they are putting their families at risk. Knowledge of a data leak will keep families ready. Weak passwords, oversharing, unsafe apps, and unsecured networks commonly cause leaks. Some of the effects include identity theft, fraud, spam, and damaged reputation. Thus, Prevention needs good practices and effort.
Apps like FlashGet Kids will offer solutions that can assist parents in securing the digital environments for their kids. These applications facilitate tracking, restricting, and tracking whereabouts, along with healthy Internet practices. Also, Families can prevent the harmful effects of leaks by combining tools with proper education. All in all, the active practice reinforces the safety and safeguards the personal data in the digital world.

